Course Description
This course covers a number of advanced “selected topics” in the field of cryptography. The first part of the course tackles the foundational question of how to define security of cryptographic protocols in a way that is appropriate for modern computer networks, and how to construct protocols that satisfy …
This course covers a number of advanced “selected topics” in the field of cryptography. The first part of the course tackles the foundational question of how to define security of cryptographic protocols in a way that is appropriate for modern computer networks, and how to construct protocols that satisfy these security definitions. For this purpose, the framework of “universally composable security” is studied and used. The second part of the course concentrates on the many challenges involved in building secure electronic voting systems, from both theoretical and practical points of view. In the third part, an introduction to cryptographic constructions based on bilinear pairings is given.
Course Info
Instructor
Departments
Learning Resource Types
notes
Lecture Notes
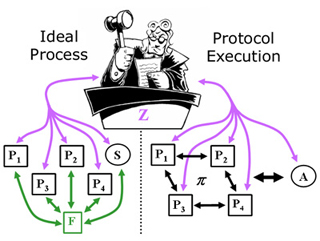
Securely realizing an ideal functionality F. (Image courtesy of Brett Paci.)








